The History of Users' IP Addresses in Windows OS
 posted by Passcape_Admin at 11:15:49 01.03.2024
posted by Passcape_Admin at 11:15:49 01.03.2024Brief overview
Understanding External IP Addresses
What is an external IP address?
The role of external IP addresses in the process of connecting to the external network
Embracing the Importance of External IP Addresses in Data Security
Discovering External IP Addresses during an Active User Session
Windows Event Logs
Network Utilities and Commands
Third-Party Security Programs
Obtaining the History of External IP Addresses when the Operating System is Inactive
Physical Access to Data Storage
Analysis of System Log Backups
Memory Analysis
Analysis of Network Devices and Logs
Modern Techniques for Retrieving IP Address Information Post Shutdown
In Conclusion
This article is available in PDF format, Chinese, French, German, Hindi, Russian and Spanish versions
Brief overview
Hello there, dear readers!
In today's digital era, where data is the currency of information exchange, security and confidentiality are paramount in our online lives. Delving into the history of users' external IP addresses is crucial for ensuring the security of operating systems, particularly on Windows. By unraveling this information, we can better understand and address potential security threats and incidents.
In the realm of computer incidents at home or in corporate environments, the history of IP addresses is a pivotal element, shedding light on potential wrongdoers and uncovering connections between various network events. This information is instrumental in forensic examinations and contributing to the overall security of the system.
In today's digital era, where data is the currency of information exchange, security and confidentiality are paramount in our online lives. Delving into the history of users' external IP addresses is crucial for ensuring the security of operating systems, particularly on Windows. By unraveling this information, we can better understand and address potential security threats and incidents.
In the realm of computer incidents at home or in corporate environments, the history of IP addresses is a pivotal element, shedding light on potential wrongdoers and uncovering connections between various network events. This information is instrumental in forensic examinations and contributing to the overall security of the system.
Understanding External IP Addresses
Before we explore the methods of acquiring the history of users' external IP addresses on the Windows operating system, it's important to grasp the fundamentals.
What is an external IP address?
An external IP address serves as a unique numerical identifier assigned to a device (for example, to your laptop) within a computer network, enabling its recognition on the global internet. In contrast to internal IP addresses, which facilitate local data exchange within a private network, external IP addresses allows devices to communicate with other entities and gain access to online resources.
The role of external IP addresses in the process of connecting to the external network
Every time a user connects to an external network, their unique IP address becomes the beacon identifying their computer in the global network, enabling data exchange with other devices and access to external resources such as websites, email, and online services. Understanding that external IP addresses can be subject to change based on factors such as the type of internet connection (e.g., dynamic or static IP address), usage of external proxy servers, and other network settings.
Embracing the Importance of External IP Addresses in Data Security
A comprehensive understanding of how external IP addresses function is indispensable in safeguarding users' data in the Windows operating system. By monitoring and scrutinizing the history of external IP addresses, potential vulnerabilities in corporate networks, unauthorized network access, VPN usage, and other security concerns can be identified, thus fortifying the protection of confidential information and personal data. Furthermore, the IP history can serve as the cornerstone for forensic examination, helping pinpoint specific user PC network access based on date, time, and address.
In the upcoming section, we will dive deeper into the methods of obtaining the history of users' external IP addresses in the Windows operating system.
In the upcoming section, we will dive deeper into the methods of obtaining the history of users' external IP addresses in the Windows operating system.
Discovering External IP Addresses during an Active User Session
In Windows operating systems, there are several widely used methods for retrieving and interpreting the history of IP addresses.
Windows Event Logs
The Windows event logs may be a crucial source of information concerning external IP addresses. These logs can record various network events, including connections to external networks. By carefully analyzing these logs, it is possible to identify irregular or suspicious activities, such as unauthorized access attempts or anomalies in network traffic. It's worth noting that by default, the Windows system components do not store the history of connections to external IP addresses. Therefore, accessing this information is only possible if the corresponding Event Log settings have been enabled in advance.
Network Utilities and Commands
Windows provides a variety of network utilities and commands that can be leveraged to trace external IP addresses. For instance, the "netstat" command allows users to monitor active network connections, revealing external IP addresses and utilized ports. This method provides valuable insights for analyzing current network connections. However, it's important to know that information collected about external connections and networks is only accessible during the active user session.
Third-Party Security Programs
Numerous specialized security programs, such as Wireshark and NetworkMiner, are designed to analyze and monitor network activity. These programs offer advanced functionality, including intrusion detection, network traffic analysis, anomaly detection, and much more. Similar to the "netstat" command, their use is limited to the online session of the currently logged-on user.
Obtaining the History of External IP Addresses when the Operating System is Inactive
Accessing the history of external IP addresses when the Windows operating system is not running can be a complex yet achievable task with the right tools and techniques. This section will explore several approaches that can be utilized for this purpose.
Physical Access to Data Storage
Direct physical access to the storage device containing system log data, such as Windows event logs, offers a straightforward way to access the history of external IP addresses. This is particularly valuable during incident investigations when a computer has been confiscated as evidence. Specialized programs and tools for offline log analysis can be employed to extract and analyze relevant information about external IP addresses.
Analysis of System Log Backups
If the primary data storage is inaccessible, backups of the system log, which may be stored on other media or in the cloud, can be examined for relevant information.
Memory Analysis
When a computer is turned off but its random access memory (RAM) is accessible, data about external IP addresses can potentially be extracted from the memory dump. This process requires specialized tools for memory dump and analysis and can be complex, but it can yield valuable information about the network activity that occurred at the time the computer was shut down.
Analysis of Network Devices and Logs
When access to the computer is limited, analyzing network devices such as routers or firewalls, which may log network activity, can help determine the external IP addresses with which the computer interacted before shutdown.
Each of these methods has unique characteristics and demands specific skills and tools for successful implementation. However, they may prove ineffective if the operating system was turned off or no activity logging was carried out, something that is not enabled by default.
Each of these methods has unique characteristics and demands specific skills and tools for successful implementation. However, they may prove ineffective if the operating system was turned off or no activity logging was carried out, something that is not enabled by default.
Modern Techniques for Retrieving IP Address Information Post Shutdown
Let's delve into the fundamental tools and methods used for gathering data about external IP addresses after the Windows operating system has been turned off.
Historically, the retrieval of IP connection history post-shutdown has posed a challenge as there haven't been dedicated programs capable of this, aside from some event logs analysis tools. Understandably, for security reasons, Microsoft has not stored such history in its operating systems. However, against conventional wisdom, our specialists have uncovered that data about IP addresses can still be accessed, particularly on Windows 10 and later operating systems.
The process of obtaining this information is surprisingly straightforward, even for those new to PC systems. By creating a bootable Reset Windows Password stick and selecting the 'User Activity - IP Address History' option, one can initiate the extraction process.
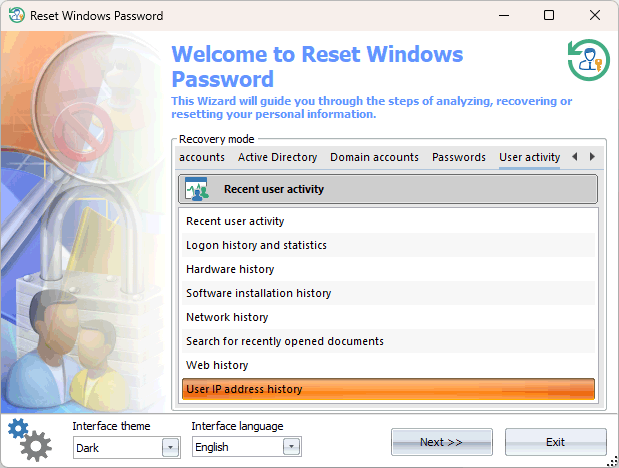
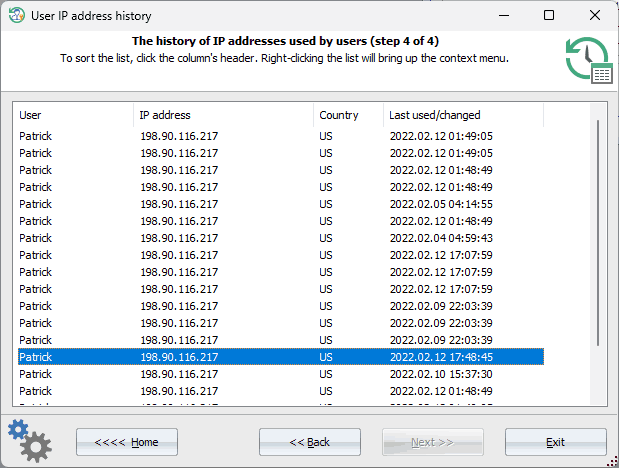
During the analysis (the IP history information is scattered across the system), the program may require the user's logon password to decrypt certain records, eventually presenting a table showcasing the discovered IP addresses, their corresponding countries, and the timestamps of network access from those IPs.
In Conclusion
Examining and decrypting IP history in the context of incident analysis within Windows operating systems is crucial for identifying and investigating potential security threats. Familiarizing oneself with this process is paramount for computer security experts when responding to incidents and safeguarding digital systems. Traditionally, accessing information about external IP addresses has demanded a combination of technological tools, monitoring systems, and network analyzers. The modern methodology outlined in this article notably streamlines this process.
To sum up, underscoring the need for continual updates and adaptation to evolving threats is crucial for computer security. Embracing and implementing modern information-gathering methods is an integral part of this process, ultimately contributing to the protection of computer systems in today's digital landscape.
Thank you for your attention, and stay safe!
To sum up, underscoring the need for continual updates and adaptation to evolving threats is crucial for computer security. Embracing and implementing modern information-gathering methods is an integral part of this process, ultimately contributing to the protection of computer systems in today's digital landscape.
Thank you for your attention, and stay safe!












