Windows Password Recovery - GPU brute-force attack
A GPU brute force attack is fully identical to a regular brute force attack, except that passwords are searched by the graphics processing unit of your PC instead. It is no secret that the performance of modern graphics cards is an order of magnitude greater than that of CPUs; this makes them a convenient tool for heavy calculations, such as password recovery. It is important to understand that calculations using graphics cards have a number of disadvantages. For example, some algorithms with a great number of conditional jumps and other checks demonstrate extremely poor performance on GPU, and in certain cases, it may be even lower than on a regular CPU.
Anyway, the software supports brute-force password search using GPU. You can compare the performance indicators of GPU vs. CPU calculations through the respective menu item of the application or present it visually through the 'Reports' menu. Recovery speed using modern video cards can reach billions (!) passwords per second.
The configuration of GPU brute force attack consists of three parts:
- Choosing a character set for the search.
- Specifying the password length.
- Configuring the graphics processing unit.
Choosing a character set for the search
When choosing a character set for a brute force attack, you are normally guided by empirical considerations. For example, if the expected password consists of lower-case Latin characters and digits, it makes sense to choose the range 'a-z, 0-9'. The smaller the character set, the sooner the attack completes.
On the other hand, there is always a chance to make a wrong choice of the expected character set. If at least one character of the password to be recovered is not included in the specified character set, the password will not be found.
At the bottom of the attack settings dialog, you can see the total number of passwords that match the specified character set and password length.
It is important to know that LM passwords in Windows are always converted to upper case; that significantly cuts the range of passwords to be searched!
Specifying password length
On the second tab of the options page, set the minimum and maximum length of searched passwords. As an alternative to the minimum length, you can set the source password, which the search would begin with. The maximum length of LM in Windows operating systems is 7.
Configuring the graphics processing unit
Before you can use it in an attack, you must first select the graphics card on the respective menu item.
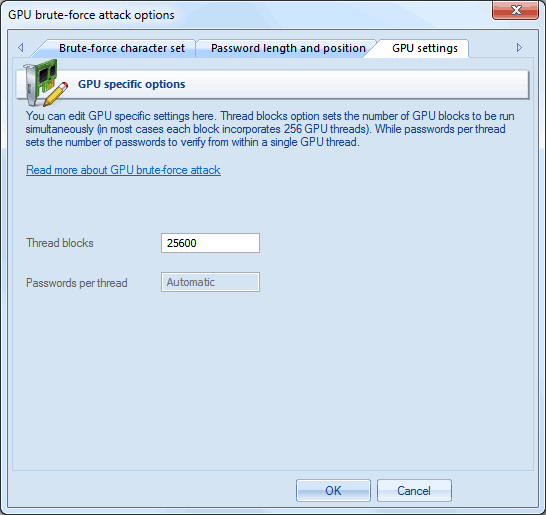
GPU configuration consists of only 1 parameter: the number of thread blocks to run on GPU. Each block consists of 256 threads. Thus, if you set the number of blocks to 25600, the GPU will run 25600*256=6553600 threads. Each GPU thread can check multiple passwords. The total number of checked passwords greatly depends on other options. Setting the ThreadBlocks parameter smaller than 10000 on modern graphics cards, in the majority of cases, leads to poor performance. To avoid performance degradation, after setting up the parameter and running the attack, make sure the GPU load chart has close to 100% plain graphic without peeks (see the sample below).