Mozilla Master Password Recovery Screenshots:
choosing Mozilla Master Password decryption method
Decryption method
The program currently supports 7 primary decryption types:
-
Artificial Intelligence Attack is a new type of attack developed by our company. It is based upon a social engineering method and allows, without resort to time-consuming and costly computations, to almost instantly recover certain passwords.
-
Dictionary attack is the most efficient recovery method, when the program tries each word from the dictionary (or dictionaries). This method is the most efficient since many people use regular words or phrases for their passwords.
-
Brute-force attack. During the brute-force attack, the program uses all possible combinations from the specified range of characters. For example, for a four-character range of lower-case Latin characters, it will check all possible combinations, starting with 'aaaa', 'aaab', 'aaac', and all the way through 'zzzz'. Totally 26^4 + 26^3 + 26^2 + 26 = 475 254 password combinations. This is the slowest attack, so it is really great for short and simple passwords.
-
Mask attack. This type of attacks is useful if you have at least some information about the password. It is a variation of the brute-force attack, except that some characters for finding the password remain unchanged, and only a portion of the password may change. For example, you may know that the first four characters in the passwords are Latin letters; they are followed by a three-digit number.
-
Base-word attack (developed by Passcape). Unlike the previous attack, here you do not have to set a mask - just provide a basic word the password may consist of. The program will take care of the rest. The phrase attack is based upon the experience of the social engineering and uses over 140 rules for possible modifications of the original phrase to generate a great number of possible password combinations.
-
Combined dictionary attack (developed by Passcape) uses to guess difficult and compound passwords. It is very similar to the dictionary attack, except that instead of using a single word for password verification it uses a combination of words created by combining words from several dictionaries.
-
The idea of the phrase attack (developed by Passcape) is to guess the right password by searching through predefined frequently used expressions, phrases, and word combinations.
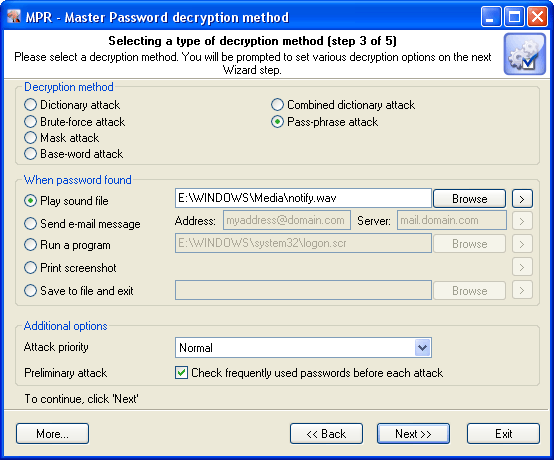
When password found
This group allows setting an action to be performed automatically when the password is found. There are five possible notifications: play sound, send e-mail, run application, print screen or store results to file.
Additional options
In the Additional options group you can specify:
-
Attack priority. If you are planning on using your computer actively during an attack, we recommend setting the priority value to 'Below normal' or even 'Low'.
-
Preliminary attack. Check the most frequently used passwords before each attack. Selecting this option, you will activate the preliminary attack. The preliminary attack consists of several mini sub-attacks and allows to find out simple and frequently used passwords like 'qwerty'.