Hacking WPA2 passwords on Apple iOS in just a few seconds
 posted by Passcape_Admin at 09:33:24 19.06.2013
posted by Passcape_Admin at 09:33:24 19.06.2013
In researching Apple iOS the German security experts Andreas Kurtz, Daniel Metz, and Felix C. Freilin have discovered just how the iOS operating system generates WPA2 passwords for establishing a wireless connection for WiFi mobile hotspots.
In such cases, external devices are connected to the Apple iOS using a unique PSK (pre-shared key). Unauthorized devices cannot connect to a protected hotspot.
As it turned out, the WPA-PSK is not generated randomly at all, but on the basis of a dictionary. Four random digits are then added to the word. In addition, some words appear in the generated passwords much more often than others. Ten of the most often used words constitute 5% of the passwords. Funny, but actually only 1842 words are used for generating WPA pass-phrase.
Taking into account such a limited range of the WPA-PSK generation, it only takes minutes or even seconds using the up-to-date video cards to search through all 1842*10000=18.43 million combinations.
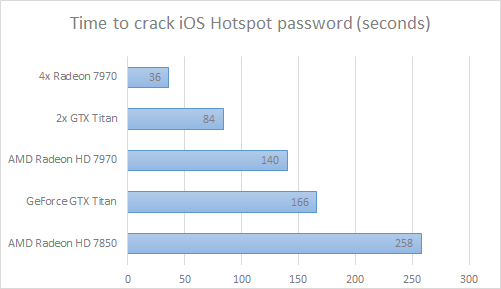
See the table below for approximate times to crack a password using various GPUs.
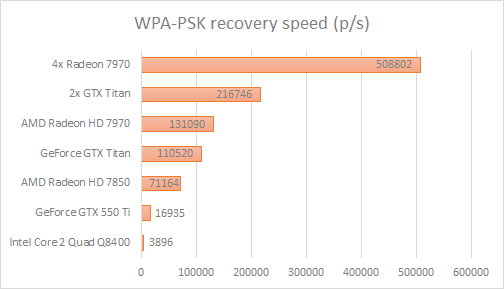
The table below shows the WPA-PSK recovery speed using our Wireless Password Recovery tool.