Implementation flaw in Windows Hello biometrics
 posted by Passcape_Admin at 10:09:02 02.09.2022
posted by Passcape_Admin at 10:09:02 02.09.2022Brief overview
OSes affected
What is Windows Hello biometrics?
What is DPAPI?
Description of the mis-implementation in Windows Hello biometric authentication
What data is at risk?
PoC
Conclusion
This article is available in PDF format, Chinese, Hindi and Russian versions
Brief overview
Using Windows Hello biometric authentication compromises all personal data encrypted with DPAPI.OSes affected
If the TPM protection is not set, all versions of Windows 10 and 11 are affected, all local accounts, as well as Microsoft and Azure AD ones.
What is Windows Hello biometrics?
Unlike a common password authentication, Windows Hello biometrics is a new, easy and supposedly safer way to sign into Windows using your unique physical characteristics. The Windows Hello was first introduced in Windows 10 and included fingerprint and face recognition technology.
The Windows Hello allows users to securely log into devices that have the necessary hardware components without having to type a password. You will have to work hard to forget or alter your biometric data, because it's an integral part of your personal identity. Moreover, the biometric authentication, either facial recognition or fingerprint scanning, is more convenient and faster compared to the process of typing a password.
The Windows Hello allows users to securely log into devices that have the necessary hardware components without having to type a password. You will have to work hard to forget or alter your biometric data, because it's an integral part of your personal identity. Moreover, the biometric authentication, either facial recognition or fingerprint scanning, is more convenient and faster compared to the process of typing a password.
What is DPAPI?
Data Protection Application Programming Interface is a primary data protection subsystem in all Windows Operating System since Win2K. DPAPI is used both by applications to protect their private information against the prying eyes and by the system to keep your personal data safe and secure. Such as network passwords, digital certificates and private encryption keys, authentication tokens, etc. If you want to deep down into the way the DPAPI works, refer to our blog-post dedicated to DPAPI algorithms and principles.
Description of the mis-implementation in Windows Hello biometric authentication
Windows 10 - 11 DPAPI implementation is fully compatible with Windows Hello biometric authentication. So it's possible, besides using your logon password, to decrypt any DPAPI-protected data directly with a fingerprint or a facial recognition. The problem is that neither a fingerprinting nor a facial recognition is required to do that, since the user profile directly stores everything necessary for the successful decryption. Assuming that the appropriate authentication method has been configured for the user account previously.
What data is at risk?
All DPAPI-protected data is at risk as soon as all the following conditions are met:- The source operating system is Microsoft Windows 10 or higher;
- The user account type is local, Microsoft, or Azure AD;
- The user account is configured to log in using Windows Hello biometrics;
- The TPM protection is off;
Some examples of the personal data protected by DPAPI
- Passwords to websites, cookies and credit cards stored by the popular browsers: Google Chrome, Microsoft Edge, Opera browser, etc.
- Passwords for some popular e-mail clients. Such as Microsoft Office Outlook, Windows Mail. Encryption keys for S-MIME.
- Credentials to shared resources.
- Encryption keys and passwords stored in Windows Vault.
- Remote Desktop credentials.
- EFS encryption keys.
- Users' personal certificates.
- Network credentials stored in Credential Manager. Including authentication tokens and other private information.
- Personal data in any application that uses DPAPI, such as Skype, Windows Rights Management Services, Windows Media and so on.
PoC
Here's a step-by-step instruction on how to decrypt a DPAPI blob without knowing the user logon password.Attach an external disk drive with the biometric account to your PC. In the case of a virtual disk, make sure it has read-write permissions. Otherwise, the program will not be able to extract any data from Windows Hello protected directories. On the screenshots below, the system assigned letter F: for the externally connected drive.
Run the Windows Password Recovery, locate the menu 'Utils', and then 'DPAPI decoder and analyzer -> Decrypt DPAPI data blob'
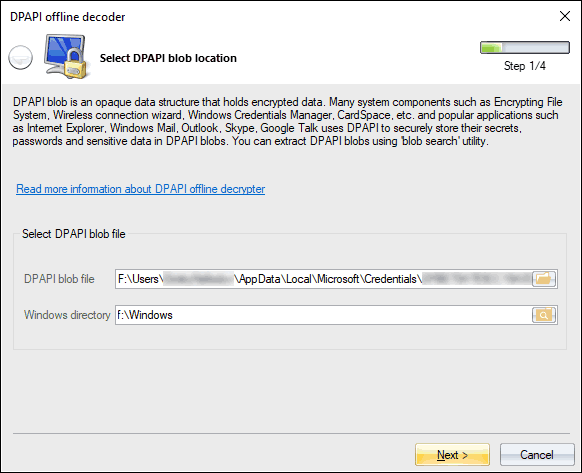
Provide the path to the DPAPI blob you need to decrypt and to the Windows directory.
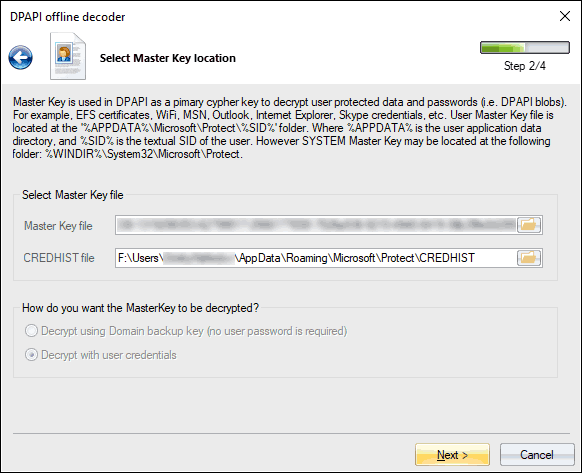
In the next dialog, specify the path to the master key. All user's master keys live in %USER_PROFILE%\AppData\Roaming\Microsoft\Protect folder.
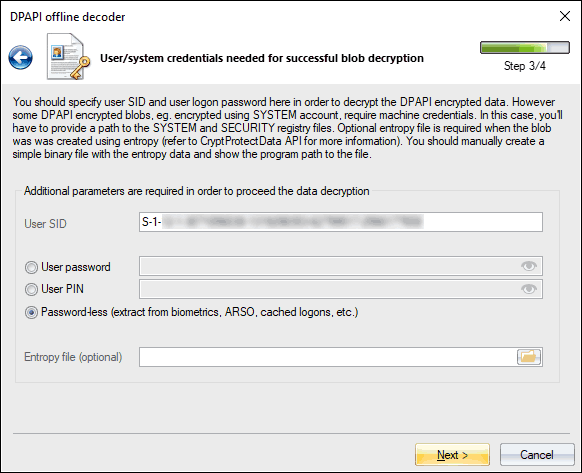
Now select the 'Password-less' and click the 'Next' button to finalize the decryption.
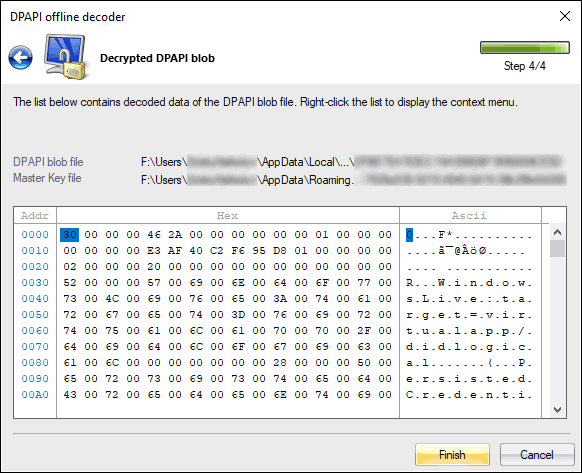
Conclusion
Despite all Microsoft's assurances about the safety of the biometric authentication, we see that this is not quite true, to put it mildly.
If your account uses a biometric authentication with the TPM protection set off, be extremely careful. All your personal data is at potential risk!
To protect your personal information, consider setting on a full disk encryption, turning the TPM protection (of course, if your hardware supports it) or stop using the biometric authentication at all.
If your account uses a biometric authentication with the TPM protection set off, be extremely careful. All your personal data is at potential risk!
To protect your personal information, consider setting on a full disk encryption, turning the TPM protection (of course, if your hardware supports it) or stop using the biometric authentication at all.












