Password Recovery - hybrid dictionary attack
Hybrid dictionary attack is a form of simple dictionary recovery. However, unlike the latter, hybrid recovery allows a user to set his own word mutation rules. For example, you could capitalize the first letter of a password being validated, append '123' to it, replace the number 0 in it with the letter O, B with 8, etc.
Actions, performed on words from the source wordlist, are called rules.
Multiple rules can be applied to each source word.
Hybrid dictionary attack settings are grouped in 7 tabs:
- Dictionaries - for setting up source wordlists.
- Rules - files with a set of rules.
- Super-rules - ones to be applied over the top of regular rules.
- Dictionary generator, where you can create files of words obtained from the hybrid attack.
- Online dictionaries - for downloading new dictionaries to be used by the attack.
- Attack syntax - complete description of all rules with examples.
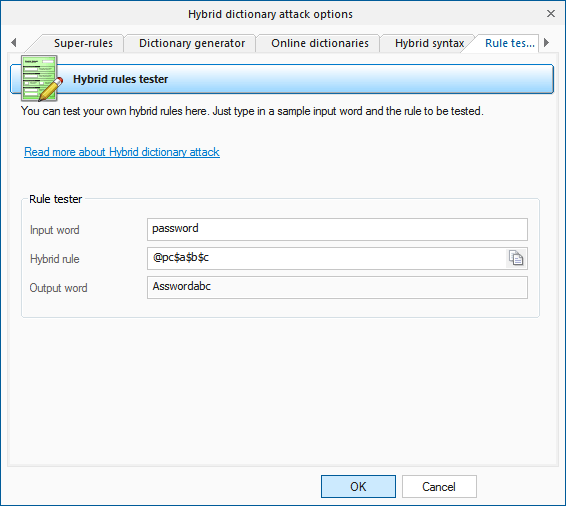
- Rule tester, where you can test your rules.
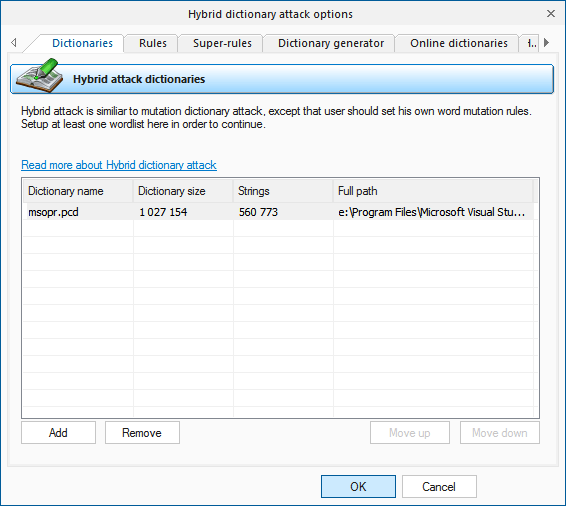
Dictionaries
Wordlists to be used in the attack are set on the first tab. The program supports wordlists in ASCII, UTF8, UNICODE, PCD, RAR and ZIP format. The position of the files on the list can be altered. For example, you may want to move smaller wordlist up the list or the other way. During the recovery, they will be used one after another, according to their position on the list.
Rules
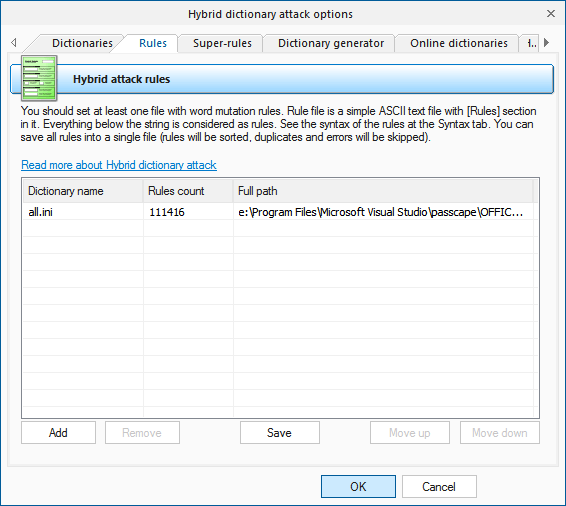
On the Rules tab, you should define at least one file with password mutation rules. The format of the rules file is quite trivial; it is a plain-text ASCII file with the '[Rules]' string. Anything above this string is considered comments and ignored by the program. Whatever goes below this string is considered rules. Each string can contain several rules, applicable to a source word. If a string contains multiple rules per word, those rules are parsed left to right. For example, if you apply the rule '@pc$a$b$c' to the source word 'password', at the output you will get 'Asswordabc'.
The maximum length of an output word may not exceed 256 characters.
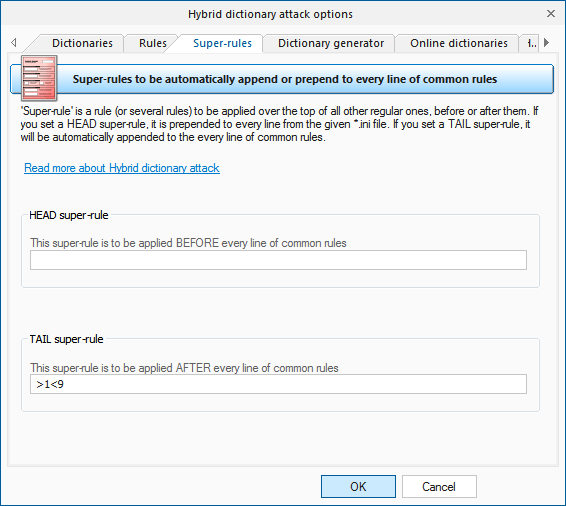
Super-rules
'Super-rule' is a rule (or several rules) to be applied over the top of all other regular ones, before or after them. For example, you can set 'a8' tail super-rule to create all possible case combinations after a common mutation has been done. So '/asa4' rule from l33t.ini file will become '/asa4a8', '/csc(' will become '/csc(a8', etc. Yet another one example: setting the '>8' head rule allows you to skip all words of less than 8 or greater than 16 characters, before starting a common mutation. This is a helpful feature once you decide to add the same rule to all text lines of the selected *.ini files. There's no need to modify them all.
Be careful though, the 'aN' super-rule may increase the total number of generated passwords drastically (hundreds or even thousands of times).
Dictionary generator
The 'Dictionary generator' tab is designed for generating wordlists to be used in other programs for example. To generate a wordlist, specify a source dictionary and a set of mutation rules for it. The program supports large files (over 2 Gb).
Be careful, the dictionary generation process may take considerable time!
Online dictionaries
You can download additional wordlists for the attack using 'Online dictionaries' tab.
Syntax
If you want to create your own set of rules, you can use the last two tabs as sources of help. While the 'Syntax' tab gives mere descriptions of available rules, on the last tab you can actually test them by specifying a word and a rule to be checked.
Rules description for the hybrid dictionary attack
- Several rules at a line are allowed to be set.
- Rules are processed from the left to the right.
- Maximal line length is limited to 256 characters.
- Maximal output word length is limited to 256 characters.
- All text before the [Rules] line is considered as a comment.
- White space is ignored as long as it is not used as a parameter.
- A line started with # character considered as a comment.
- N and M always start at 0. For values greater than 9 use A..Z (A=10, B=11, etc.)
Forward your rule files to us; if we find them interesting, we will include them in the default distribution of the program.
Rules
| Rule |
Example |
Input |
Output |
Description |
| : |
: |
password |
password |
Do nothing to the input word. |
| { |
{ |
password |
asswordp |
Rotate the word left. |
| } |
} |
password |
dpasswor |
Rotate right. |
| [ |
[ |
password |
assword |
Delete the first character. |
| ] |
] |
password |
passwor |
Delete the last character. |
| c |
c |
password |
Password |
Capitalize. |
| C |
C |
password |
pASSWORD |
Anti-capitalize - lowercase the first character, uppercase the rest. |
| d |
d |
password |
passwordpassword |
Duplicate word. |
| f |
f |
password |
passworddrowssap |
Reflect word. |
| k |
k |
password
пароль |
зфыыцщкв
gfhjkm |
Convert word using alternative (first after default) keyboard layout. The rule works in both directions. For example, if there's Russian keyboard layout installed previously in the system, the rule should convert word 'password' to Russian 'зфыыцщкв', and Russian word 'пароль' to 'gfhjkm'. This is very helpful when looking for non-English passwords. If only one language is installed in the system, the rule does nothing. |
| K |
K |
password |
passwodr |
Swap last two characters. |
| l |
l |
PassWord |
password |
Convert all characters to lowercase. |
| q |
q |
password |
ppaasssswwoorrdd |
Duplicate all symbols in a word. |
| r |
r |
password |
drowssap |
Reverse word. |
| t |
t |
PassWord |
pASSwORD |
Toggle case of all characters |
| u |
u |
password |
PASSWORD |
Convert to uppercase. |
| U |
U |
my own password |
My Own Password |
Capitalize all words delimited with space (upper-case the first character and every character after space). |
| V |
V |
password |
PaSSWoRD |
Vowels elite. |
| v |
v |
password |
pASSWoRD |
Vowels noelite. |
| |
|
| 'N |
'4 |
password |
pass |
Truncate the word to N character(s) length. |
| +N |
+1 |
password |
pbssword |
Increment character at position N by 1 ASCII value. |
| -N |
-0 |
password |
obssword |
Decrement character at position N by 1. |
| .N |
.4 |
password |
passoord |
Replace character at position N with character at position N+1 |
| ,N |
,1 |
password |
ppssword |
Replace character at position N with character at position N-1. Where N > 0. |
| |
|
|
|
Reject (skip) the word if it is greater than N characters long. |
| >N |
|
|
|
Reject (skip) the word if it is less than N characters long. |
| aN |
a8 |
|
|
Check all possible symbol cases for the word. N is a maximal length of the word to apply this rule for. |
| DN |
D2D2 |
password |
paword |
Delete the character at position N. |
| pN |
p3 |
key |
keykeykey |
Copy word N times. |
| SLN |
SL2 |
012345678 |
01d345678 |
Bitwise shift left character at position N. |
| SRN |
SR2 |
password |
pa9sword |
Bitwise shift right character at position N. |
| TN |
T1T5 |
password |
pAsswOrd |
Toggle case of the character at position N. |
| yN |
y3 |
password |
paspasword |
Duplicate first N characters. |
| YN |
Y3 |
password |
paswordord |
Duplicate last N characters. |
| zN |
z3 |
password |
ppppassword |
Duplicate the first character of the word N times. |
| ZN |
Z3 |
password |
passwordddd |
Duplicate the last character of the word N times. |
| |
|
| $X |
$0$0$7 |
password |
password007 |
Add character X to the end of the word. |
| ^X |
^3^2^1 |
password |
123password |
Insert character X at the beginning of the word. |
| @X |
@s |
password |
paword |
Remove all characters X from the word. |
| !X |
!. |
|
|
Reject (skip) the word if it contains at least one character X. |
| /X |
/1/2/3 |
|
|
Reject (skip) the word if it does not contain character X. |
| (X |
(p |
|
|
Reject (skip) the word if the first character is not X. |
| )X |
)d |
|
|
Reject (skip) the word if the last character is not X. |
| eX |
e@ |
mike@yahoo.com |
mike |
Extract a substring starting at position 0 and ending up before the first occurrence of X character (do nothing if X is not found). |
| EX |
E@e. |
mike@yahoo.com |
yahoo |
Extract a substring starting right after first found X character and till the end of the string (do nothing if X is not found). |
| |
|
| %MX |
%20 |
|
|
Reject (skip) the word if it does not contain at least M instances of the character X. |
| *XY |
*15 |
password |
possward |
Swap characters at positions X and Y. |
| =NX |
=01 |
|
|
Reject (skip) the word if the character at position N is not equal to the X |
| iNX |
i4ai5bi6c |
password |
passabcword |
Insert the character X in position N. |
| oNX |
o4*o5* |
password |
pass**rd |
Overwrite a character in position N with the character X. |
| sXY |
ss$so0 |
password |
pa$$w0rd |
Replace all characters X with Y. |
| xNM |
x4Z |
password |
word |
Extract a substring of up to M characters length, starting from position N. |
| |
|
|
|
|
| INX-Y |
rI0/-/r |
google.com |
google.com/ |
Insert the character X at position N if the previous character at position N is not Y. |
| INX+Y |
rI0.+.r |
password. |
password.. |
Insert the character X at position N if the previous character at position N is Y. |
| ONX-Y |
O0-+p |
password |
-assword |
If the character at position N is not Y, overwrite it with X character. |
| ONX+Y |
O0P+p |
password |
Password |
If the character at position N is Y, overwrite it with X character. |
| RNM+Y |
R01+a |
password |
assword |
Remove character at position N if the character at position M is Y |
| RNM-Y |
R40-b |
password |
passord |
Remove character at position N if the character at position M is not Y |





