Password Recovery - preliminary attack
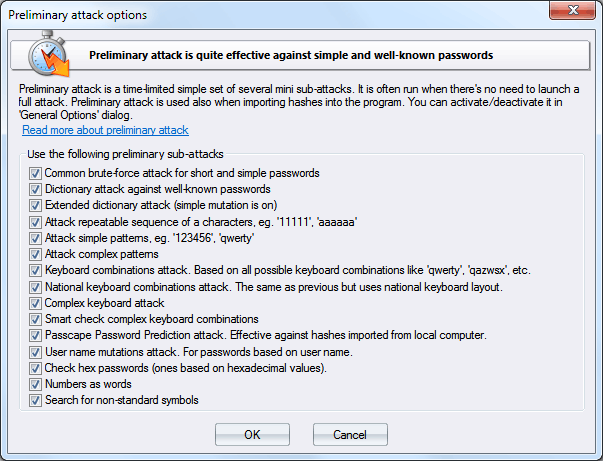
Preliminary recovery (developed in our company) is quite effective against short, simple, dictionary, repetitive, keyboard, etc. passwords and consists of several mini-modules. You can turn on/off each mini-attack separately.
Preliminary attack runs about 20-30 minutes (depending on the hardware used and password hash algorithm) or even faster.
Mini-modules of the Preliminary recovery:
- Attack against names. Verify various combinations of the document/user/network (or whatever) name.
- Dates attack. Checks passwords that were based on date. For example, 12031994.
- Simple dictionary attack. Fast check the password by verifying all words from a given wordlist.
- Attack on repeatable. Checking passwords as a repeatable sequence of a character. Eg. '1111111' or 'xxxxxxx'.
- Attack on simple character patterns, like '123456' or 'qwerty'.
- Attack on complex character patterns, like '123qaz' etc.
- Keyboard attack looks for keyboard passwords and all possible combinations. Eg. 'qwer', 'qazwsx', 'asdzxc', etc.
- The same as above but checks international passwords.
- Complex keyboard attack is the same as the previous 2 attacks but checks compound keyboard patterns.
- Smart keyboard attack guesses complicated keyboard combinations.
- Passcape Password Prediction attack is the most complicated and state-of-art password prediction tool.
- Attack passwords based on numbers.
- Attack against short passwords based on hexadecimal values.

