Reset Windows Password v14.2
Telegram data recovery, Photo Database and Media Player investigation tools, and some more
Windows CardSpace - reading system credentials
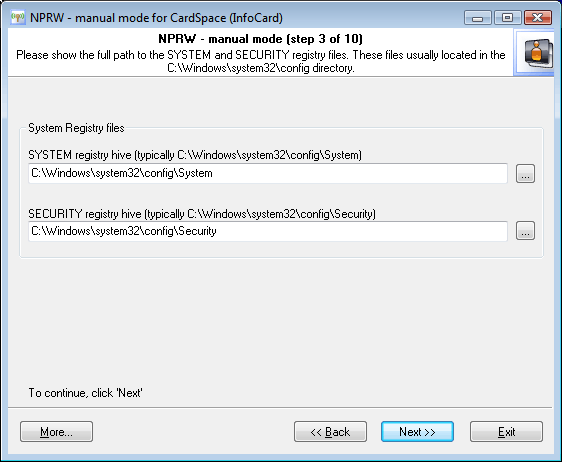
Any account in Windows, whether that's a user or the system, has the right to exist only when the corresponding passwords are set, even if those passwords are blank. System's accounts hide their passwords in Windows Secrets - a special storage for private information, inherited from the good old Windows NT.
In the automatic mode, the application reads that data automatically, without the user's participation. In our case, we are to set the path to two registry files: SECURITY, which stores secrets (we are interested in just one secret that stores the password to the system account), and SYSTEM with the system data necessary for decrypting those. By default, registry files reside in the Windows folder; to be precise, in %WINDIR%\system32\config. |