Reset Windows Password v14.2
Telegram data recovery, Photo Database and Media Player investigation tools, and some more
Reset Windows Password: Remote Desktop credentials
Selecting user account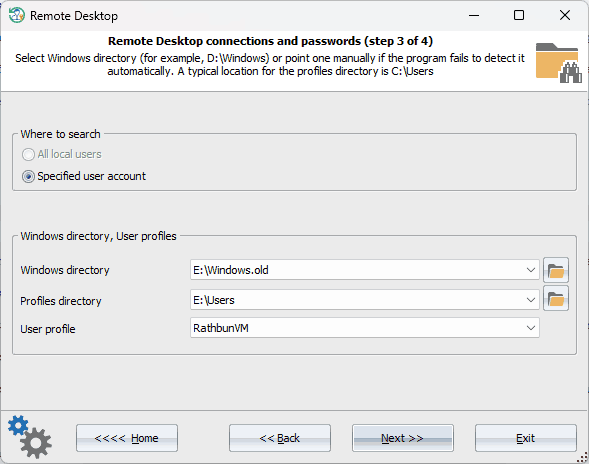 Firstly, input the Windows directory and the user account to be scanned for saved RDP credentials. Remote Desktop connections and passwords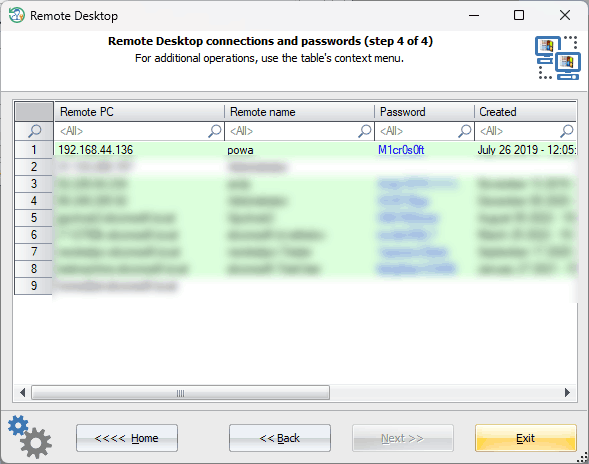
If required, provide the account logon password. The program will output all decrypted RDP credentials, along with the address of the remote computer, date connected, and other relevant information. If you need to decrypt other passwords stored in the Windows Credential Manager, switch to the network password recovery tool.
|
