Reset Windows Password: custom recovery
Once the custom recovery option is set, the program can additionally run 3 different attacks to guess the passwords:
- Dictionary attack
- Hybrid attack
- Mask attack
Dictionary attack
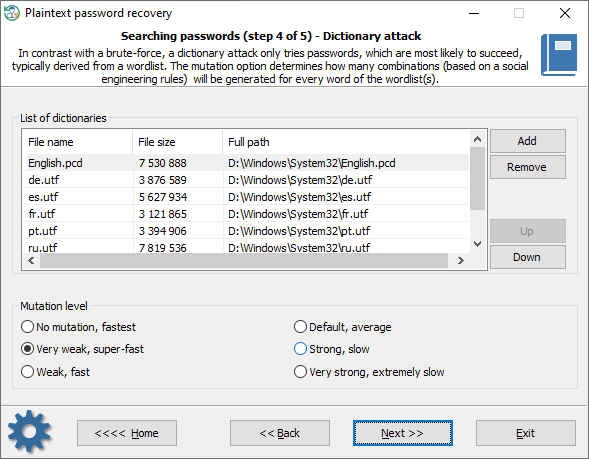
A dictionary attack tries passwords, which are most likely to succeed, typically derived from a wordlist. Reset Windows Password supports different types of dictionaries: ASCII, UNICODE, UTF8, as well as encrypted/compressed dictionaries in the native PCD format. You can use both predefined and custom dictionaries. To add your own wordlist, copy one to a USB drive and attach the drive to the target PC. The mutation level determines how many combinations (based on social engineering rules) will be generated for every word of the wordlist(s).
Hybrid attack
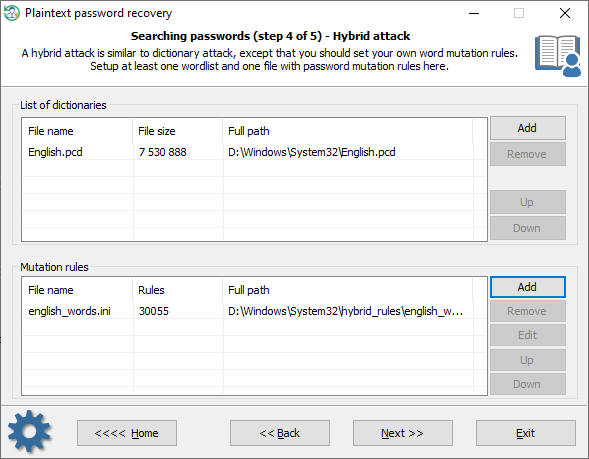
A hybrid attack is similar to a dictionary one, except that you can set your own word mutation rules. The program comes with a huge set of rule files. Just use one that is best for your task. The good thing in a Hybrid attack is that you can additionally create, edit and modify password mutation rules according to your needs.
Mask attack
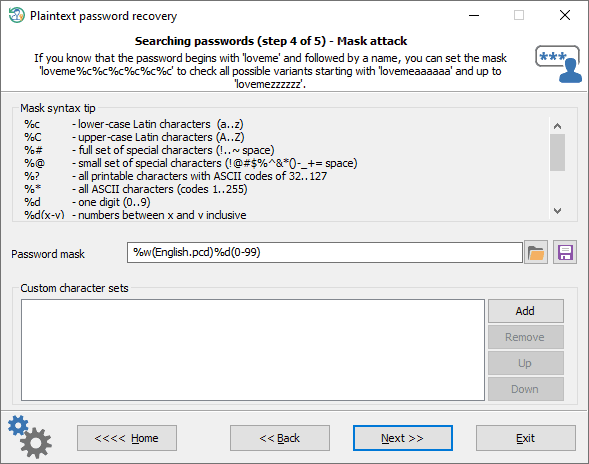
A Mask attack is an irreplaceable tool when you know a part of the password or have any specific details about it. For example, if you know that the password consists of 12 characters and starts with 'loveme', obviously it's just enough to guess the last 6 characters of the password. That is what the mask attack is for. In our example, you can set the following mask: loveme%c%c%c%c%c%c
Refer to
this page to get more detailed information on how the mask works and its syntax.



