Reset Windows Password v14.2
Telegram data recovery, Photo Database and Media Player investigation tools, and some more
Reset Windows Password: Decrypt Telegram password
Choosing recovery attacks and methods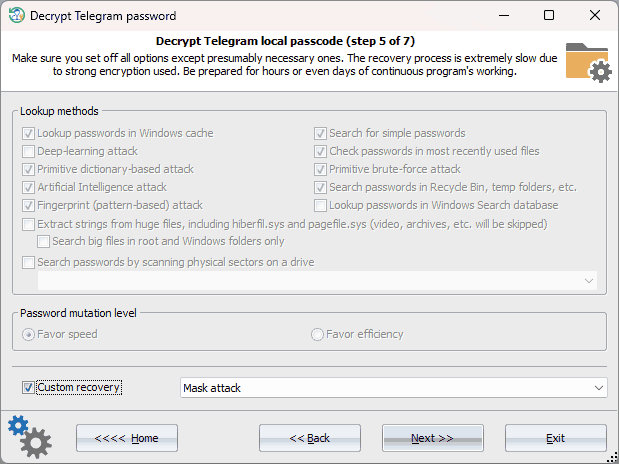
Telegram passcode has strong built-in protection. Brute-forcing such passwords runs at a rate of only a few passwords per second, which means that it is essential to choose an appropriate recovery method first. Otherwise, the process could take an indefinitely long time. If any information is available about the target passwords, it is recommended to utilize custom attacks. If not, you can switch to standard recovery, disabling the most time-consuming options, (such as primitive bruteforce and fingerprint attacks, searches in Recycle bin and temporary folders, etc.) while leaving at least two essential options: looking up for passwords in the Windows cache and using Artificial Intelligence attacks
Setting up folders or user attacks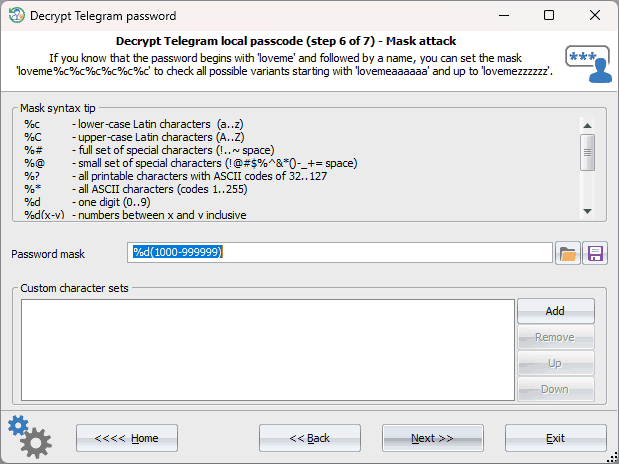
If one of the custom attacks is chosen, it is necessary to configure its parameters first. For instance, in the picture above, the mask attack is specified, which will iteratively check digital passwords from 4 and up to 6 characters long. That is, from '0000' to '999999'.
Searching for Telegram passcode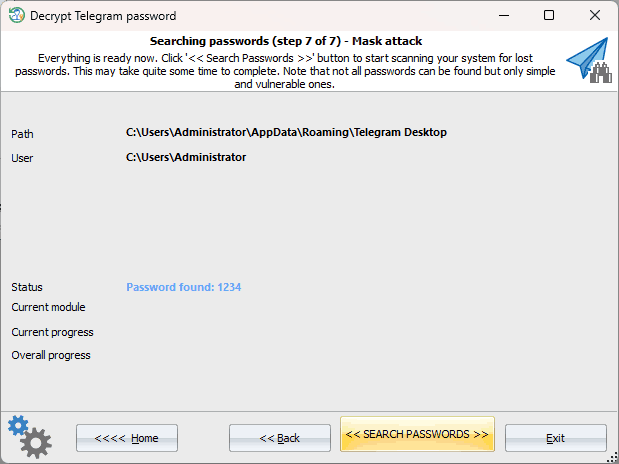
Although the algorithms used in Telegram passcode encryption are highly optimized for speed, brute-forcing can still take a significant amount of time. Interestingly, the program is much faster than the popular Hashcat tool. However, unfortunately, the bootable environment is currently restricted to utilizing the CPU only, with no option available to leverage more powerful graphics cards. |
