Windows Password Recovery - dump credentials history hashes
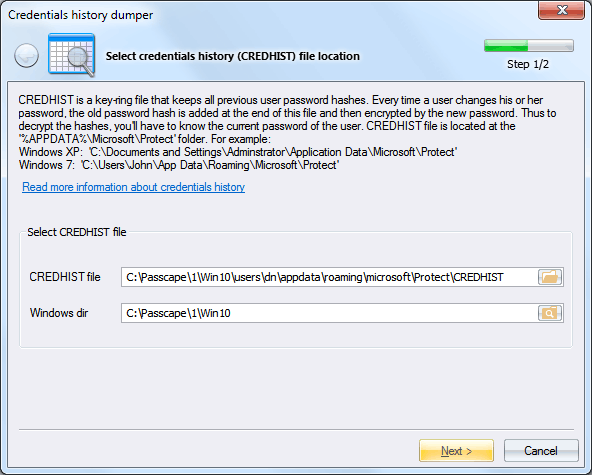
Due to peculiarities of DPAPI implementation, in order to guarantee the successful decryption of all DPAPI blobs, Windows must store all user's previous passwords in the system. User's password history is located in the following file: %APPDATA%\Microsoft\Protect\credhist
All user's older passwords (along with certain service data) are stored as pairs of hashes: SHA1 and NTLM. Moreover, in order to decrypt the last pair, you must know the hash of user's current password, to decrypt the previous hashes, you need the last decrypted pair, and so on, along the line.
Windows Password Recovery is the world's first utility, which allows decrypting password history hashes from CREDHIST files.
To do so, on the first step of the application's wizard, specify the path to your CREDHIST file and Windows folder.
Then you can decrypt and save hashes from CREDHIST to a textual PWDUMP-like file, if saving as NTLM is selected, or to a plain-text file if the SHA1 hash format is selected.
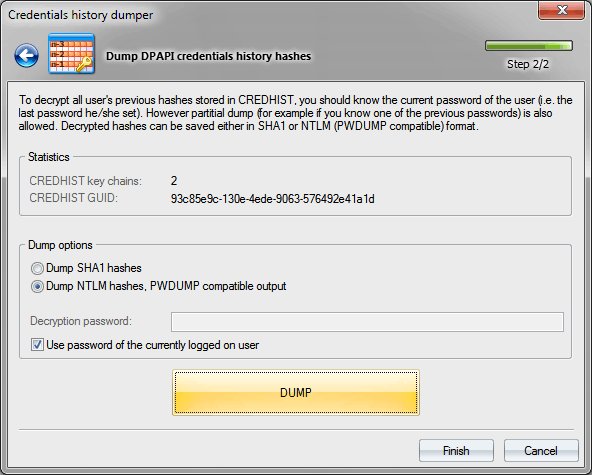
It is important to know that in order to decrypt CREDHIST hashes you must know the user logon password or PIN. If you are decrypting CREDHIST of a currently logged on user, make sure setting up the respective option. In this case, you will not have to enter the decryption password, it will be retrieved from the system cache.
The program supports partial dump of history hashes. That means that if the user's current password/PIN is unknown, but at least one of the older passwords is available, the program can decrypt the passwords the user used earlier, i.e. before that old password was entered.
Be aware, In Windows 8 and higher OSes, the dumped hashes for LiveID/Microsoft/AzureAD accounts do not correspond to those ones derived from the logon password!


