Windows Password Recovery - preliminary attack
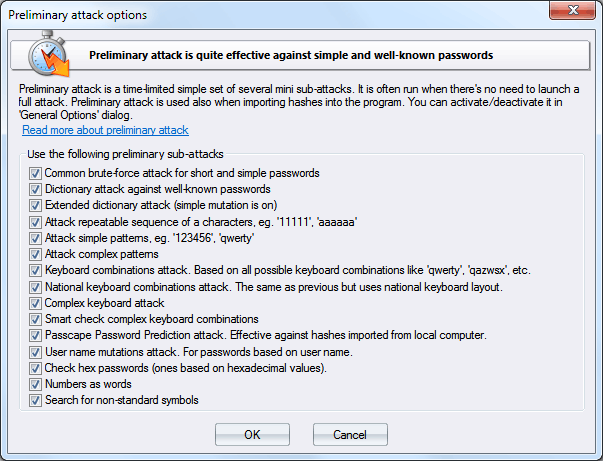
Preliminary attack (developed in Passcape Software) is quite effective against short, simple, dictionary, repetitive, keyboard, etc. passwords and consists of several mini-attacks. Each mini-attack can be enabled/disabled individually.
Preliminary attack runs about 5-10 minutes or even faster. It consists of at least the following sub-attacks:
- Common brute-force attack. Performs several simple brute-force attacks based on predefined character sets.
- Simple dictionary attack. Fast check the password by verifying all words from a given dictionary.
- Extended dictionary attack. It's almost the same as above but with some smart mutation options set on.
- Attack on repeatable symbols. Checking passwords as a repeatable sequence of a character. Eg. '1111111' or 'xxxxxxx'.
- Attack on simple patterns, like '123456' or 'qwerty'.
- Attack on complex patterns. The same as above, for compound patterns.
- Keyboard attack checks for keyboard passwords and all possible combinations. Eg. 'qwer', 'qazwsx', 'asdzxc', etc.
- National keyboard attack. The same as above, but checks passwords typed in national keyboard layout.
- Complex keyboard attack is the same as the previous 2 attacks, for compound keyboard patterns.
- Passcape Password Prediction attack is the most complicated and state-of-art password prediction tool.
- Attack on name-based passwords.
- Attack on hex passwords (eg. 7A49F3).
- Attack passwords based on numeric words.
- Search for short passwords that were created using non-standard UNICODE characters.

