Reset Windows Password v14.2
Telegram data recovery, Photo Database and Media Player investigation tools, and some more
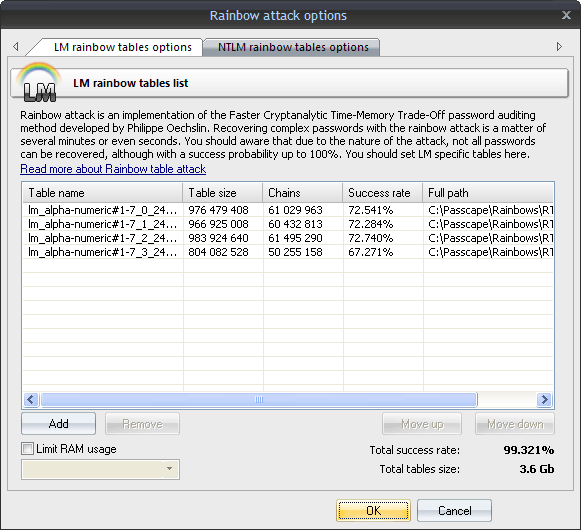
Windows Password Recovery - rainbow table attack
This is quite a sophisticated password audit tool. This method was developed by Philippe Oechslin for quick password recovery using pre-calculated tables. It's enough to say that the sought password can be recovered within minutes or even seconds. A specific rainbow table can be implemented for the hash it was created for. Eg. LM specific tables should be used for breaking LM hashes only.
The attack options allow limiting the amount of RAM that can be utilized by the attack when using old computers (the attack assumes using large volumes of RAM for its calculations). |