Windows Password Recovery - Windows Hello PIN recovery
Windows Hello enables different types of biometric sign-in: fingerprint, iris, facial or voice recognition. When you set up Windows Hello, you're asked to create a PIN first. The PIN is very well protected and is not stored anywhere in Windows 10. However, it can easily be decrypted in Windows 8. To guess a lost PIN, you should specify the Windows directory of the target system first. This could be your current Windows folder or Windows folder of an external system.
Setting Windows directory
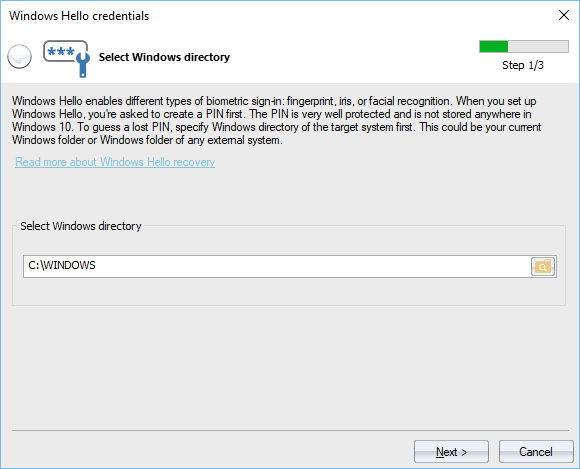
Show the Windows directory of the target system first. In order to be able to extract a PIN, the Windows directory should allow access to file change or write operations. In case you have set your current Windows folder, it is enough to run the program with Administrator privileges.
Selecting user account
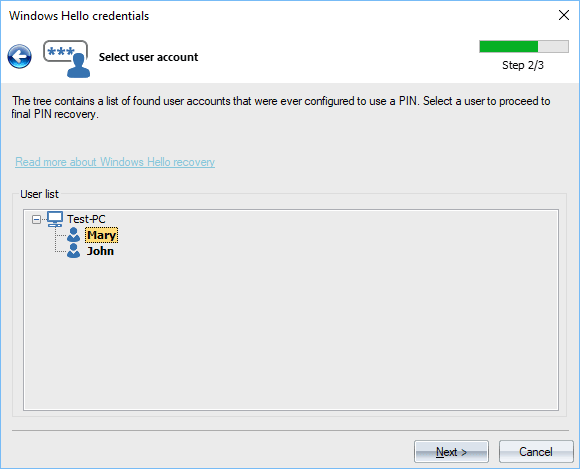
On this step, the program shows all found user accounts that have been set to use a PIN to logon into the system. Just select a user and proceed to the PIN recovery dialog.
PIN recovery
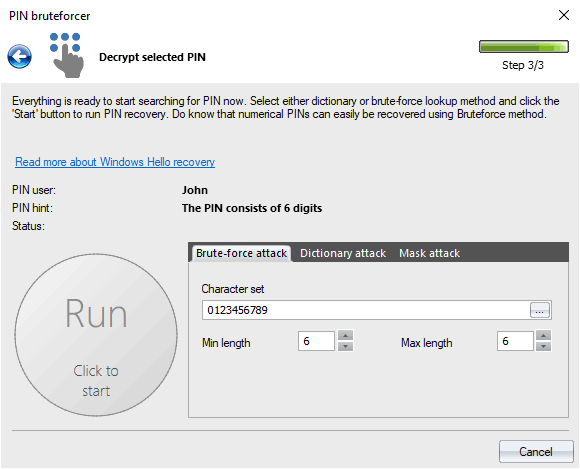
The program supports three recovery methods: brute-force analysis, dictionary guess, and search by mask. Settings for each one are rather trivial. In the case of brute-force, you will need to set up a character set, as well as minimal and maximal PIN length. For a dictionary attack, just set up a word-list and select the word mutation level required. In order to be able to run a mask attack, you should set up a recovery mask first (it assumes that you know something about the password).
To run or stop the attack, use the round button to the left of the settings.
In certain cases, the program can detect the character set used to create a PIN. If this is your case, the hint should appear in the corresponding field.
PIN codes protected with TPM are not supported since the TPM chip has built-in protection against brute-force.