Wireless Password Recovery - reading WPA hashes from local PC
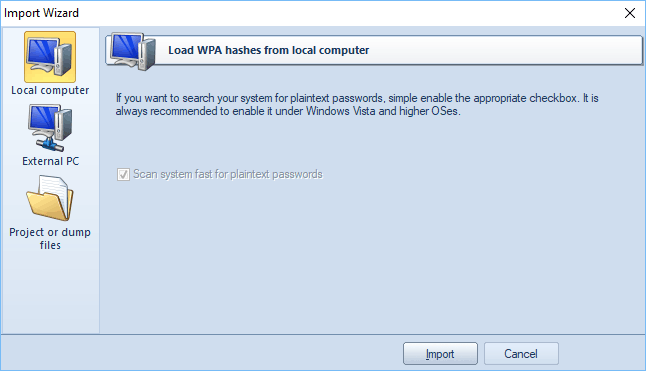
Reading hashes from the local computer is the most preferable way to extract plaintext password for Wireless connections in Windows, as it implies the deepest overall analysis of the system and the hashes. Besides, the hashes that are imported from the local computer can undergo the sophisticated Intelligent recovery, which allows recovering some WPA-PSK hashes quickly.
Local hashes load works well regardless of where the hashes are localized: in the registry (Windows XP) or in the disk (Windows Vista and higher OSes). Note that in most cases the program can decrypt plain-text passwords for WPA-PSK accounts instantly (this applies to Windows Vista and higher OSes only). The program can also extract WPA enterprise credentials (version 5.0 and newer).
The local import functionality requires administrative privileges.

