Reset Windows Password v14.2
Telegram data recovery, Photo Database and Media Player investigation tools, and some more
Reset Windows Password: Web browser history
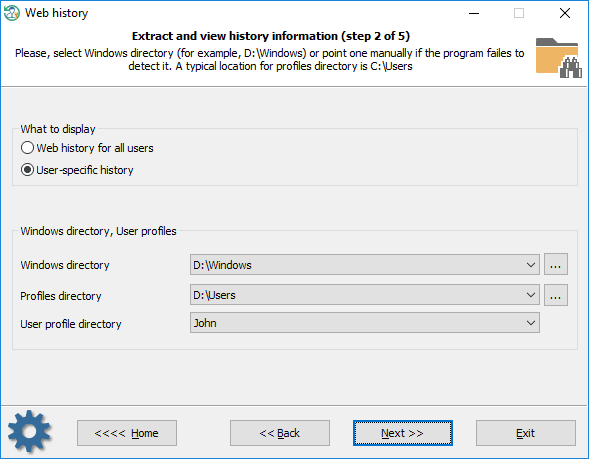
Selecting data source
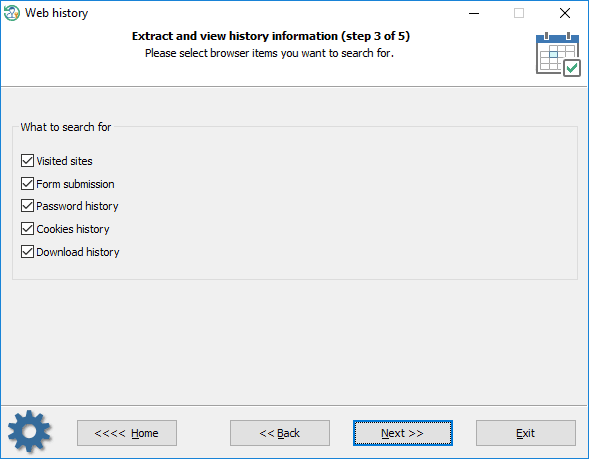
What to search for
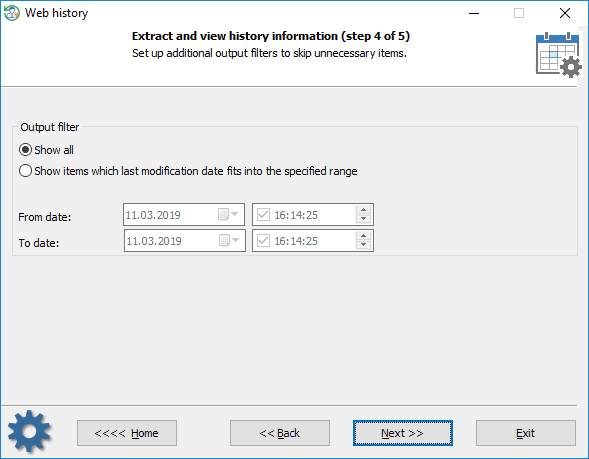
Setting up time filters
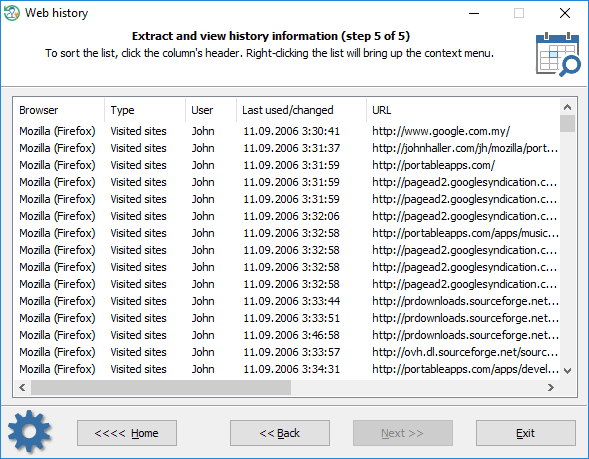
Viewing browser history
The statistics can be copied to the clipboard or saved to a file. Using the context menu, you can also hide some items that are not of interest to you.
Where do browsers store their lists of visited URLs?Internet Explorer C:\Users\%USERNAME%\AppData\Local\Microsoft\History C:\Users\%USERNAME%\AppData\Local\Microsoft\Windows\History C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Internet Explorer\UserDataOlder OSes use different paths to keep the file. Internet Explorer - typed in URLs HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TypedURLs Microsoft Edge Similar to Internet Explorer, Microsoft Edge keeps the history of the Web browsing, cache, cookies, along with other information in a single file called WebCacheV01.dat which seems to be is the successor of the index.dat. The WebCacheV01.dat is located at the following path:
C:\Users\%USERNAME%\AppData\Local\Microsoft\Windows\WebCache Opera (older versions) The browser history is kept in global_history.dat, global.dat, vlink4.dat files in the current Opera's profile. The files have different formats (depends on browser version).
Chrome (and all Chromium-based browsers) All visited URLs are kept in SQLite database called history. The location of the history is different and depends on the browser. For example: C:\Users\%USERNAME%\AppData\Local\Google\Chrome\User Data\Default Firefox (and all Mozilla-based browsers) This is either a history.dat file (a mork format) or a places.sqlite file in newer versions. A typical location is C:/Users/%USERNAME%/AppData/Roaming/Mozilla/%PROGRAM%/Profiles/%PROFILENAME%. Example:
C:\Users\%USERNAME%\AppData\Roaming\Mozilla\Firefox\Profiles\owec6tnk.default
Where do browsers store the form autocompletion data?Internet Explorer HKEY_CURRENT_USER\Software\Microsoft\Protected Storage System Provider Internet Explorer v7-9 use a different and interesting technique. Instead of encrypting user-sensitive data with a static secret key (IE 4-6) which can be figured out easily, IE 7-9 use the source URL address as the encryption key to protect the data. Thus without knowing the Web page a certain data belong to, you will not be able to decrypt the data. More details can be found here. RWP does not support extracting IE 7-9 form autocompletion data. Use our PIEPR for that. Here's the registry location where the encrypted data is stored: HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\IntelliForms\Storage1 HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\IntelliForms\FormData Internet Explorer v10+ and Microsoft Edge have even better protection. All data entries are kept in Windows Vault files and protected with DPAPI. There's no chance to decrypt it unless providing the owner logon password and master key file. A tricky part is that RWP can decrypt the data/passwords instantly if the browser has saved them under the system account. The Vault path for the user data: C:\Users\%USERNAME%\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28 Opera (older versions) The form autocompletion data can be found in the following files: C:\Users\%USERNAME%\AppData\Roaming\Opera\Profile\typed_history.xml C:\Users\%USERNAME%\AppData\Roaming\Opera\Profile\search_field_history.dat Chrome (and Chromium-based browsers) The form submission data is kept in history and Web Data files, both in SQLite format. A typical location for the Chrome browser is:
C:\Users\%USERNAME%\AppData\Local\Google\Chrome\User Data\Default Firefox (and Mozilla-based browsers) This is either a formhistory.dat file (older versions of the browser) or formhistory.sqlite file. A typical location is C:/Users/%USERNAME%/AppData/Roaming/Mozilla/%PROGRAM%/Profiles/%PROFILENAME%. Like this one:
C:\Users\\AppData\Roaming\Mozilla\Firefox\Profiles\owec6tnk.default\formhistory.sqlite
Where do browsers store their passwords?Internet Explorer HKEY_CURRENT_USER\Software\Microsoft\Protected Storage System Provider Internet Explorer v7-9 passwords are kept in the following registry key: HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\IntelliForms\Storage2 Internet Explorer v10 and Microsoft Edge default location for the saved passwords: C:\Users\%USERNAME%\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28 %SYSTEMDIR%\config\systemprofile\AppData\Local\Microsoft\Vault\4BF4C442-9B8A-41A0-B380-DD4A704DDB28 Some versions of IE can also save HTTP basic authentication passwords in the 'Credentials store' (Windows Vista and higher OSes). The DPAPI is used to protect the entries there.
C:\Users\%USERNAME%\AppData\Roaming\Microsoft\Credentials The program is smart enough to extract some extra data stored in other locations. For example, the Reset Windows Password can parse Chrome databases to look for Internet Explorer items that are kept here after data migration.
Opera (older versions) All passwords are stored in wand.dat file in encrypted form along with decryption keys. The passwords can easily be decrypted unless a Master password is set.
C:\Users\%USERNAME%\AppData\Roaming\Opera\Profile\wand.dat Chrome (and Chromium-based browsers) In Windows OSes Chromium-based browsers protect user passwords with DPAPI and store them in Login Data file which actually is an SQLite database. A typical database location for Google Chrome:
C:\Users\%USERNAME%\AppData\Local\Google\Chrome\User Data\Default\Login data Firefox (and Mozilla-based browsers) Mozilla had a long way evolving the password storage format. Initially, it was a simple textual file signons.txt. Then in version 2 it came signons2.txt which had the "#2C" prefix at the beginning. Then signons3.txt with the "#2D" prefix in version 3, etc. Next the signons.sqlite database came into a play. But it's not the end of the story. Firefox v32.x and higher has new storage for passwords - logins.json which is actually a JSON format file. In spite of apparent diversity, data protection is almost the same. A typical location for the files is:
C:\Users\%USERNAME%\AppData\Roaming\Mozilla\%PROGRAM%\Profiles\%PROFILE%.
|