Combined dictionary attack
This type of attack on difficult and compound passwords is very similar to the simple dictionary attack, except that instead of using a single word for password verification here we use a combination of words or a phrase created by combining words from specified dictionaries.
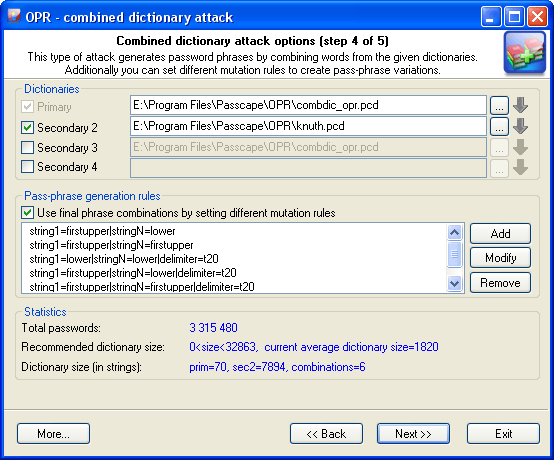
The purpose of the first group of the options is to set and choose the source material for our attack. For a start, we are to specify at least 2 dictionaries. To understand how the combined attack works, let's take a look at a couple of password generation examples that involve, in the first case, the same dictionary and in the second case - two different ones.
-
Suppose we’ve got a single dictionary with three words: aaa, bbb, and ccc. We will set this dictionary as two original sources: primary dictionary & secondary dictionary2 (see the figure). After these dictionaries have been processed, at the output we have the following phrases (they will be used when checking the password sought):
'aaa aaa', 'aaa bbb', 'aaa ccc'
'bbb aaa', 'bbb bbb', 'bbb ccc'
'ccc aaa', 'ccc bbb', 'ccc ccc'.
9 phrases total.
-
In the second case, we have got two different dictionaries. For example, the first dictionary consists of three words: aaa, bbb, and ccc. The second one also has three words: ddd, eee, fff. In this case, we are going to have the following phrases:
'aaa ddd', 'aaa eee', 'aaa fff'
'bbb ddd', 'bbb eee', 'bbb fff'
'ccc ddd', 'ccc eee', 'ccc fff'.
Hint

Perfect dictionaries for the combined passphrase attack are those that have different forms of words in them; e.g. jump, jumper, jumped, jumping.
The example is plain but demonstrative. The idea is that for multiple sources you can successfully use both a single dictionary and multiple ones. It all depends on your imagination. The last example shows that a special attention should be paid to the order of the dictionaries if they are different. The order of the words in the phrases to be created depends directly on the order of the source dictionaries. In our second example, if we swap the primary and the secondary dictionaries, at the output we will obtain a completely different set of phrases:
'ddd aaa, 'ddd bbb', 'ddd ccc',
'eee aaa, 'eee bbb', 'eee ccc',
'fff aaa, 'fff bbb', 'fff ccc'.
Combined attack sets a certain limit to the number of dictionaries that can be used; that's not more than 4. Thus, the general limitation of this attack is that only password phrases of not more than 4 words can be recovered using this attack.
Another essential drawback is the wide range of phrases generated. And, as the consequence, the proportional increase of the time spent on the validation of a password. Therefore, you should be careful when selecting the size of source dictionaries, especially for 3 and 4-word combinations.
The next group of options is in charge of creating all possible combinations of phrases. By default, if no password generation parameter based upon mutation rules is set, the program will create passwords by simply concatenating words from the source dictionaries, WITHOUT separating them with spaces. However, you can set your rules as well. For example, have it create phrases with spaces, begin words with caps, append numbers, etc. There are special rules available for this purpose; you don't have to know the syntax of them, for the mutation rule creation dialog is simple and intuitive.
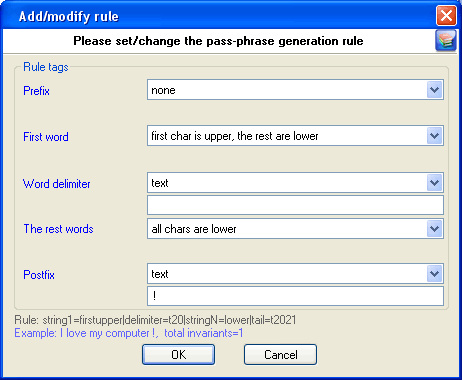
Each mutation rule consists of five elements:
- Prefix - text that will appear before each phrase. This element can be a character, plain text string, one digit between 0 and 9 or a number. For instance, if you set a one-digit prefix, the phrases created with this rules will look as follows: '0 aaa bbb', '1 aaa bbb' … '9 aaa bbb'.
- First word - the action to be performed over the first word of each phrase. There are only four options. Namely: leave intact as is in the dictionary, convert all characters to lowercase, convert all characters to uppercase or capitalize only the first letter of the word.
- Word separator. It may be absent. Then all the words will be concatenated. Example: 'aaabbb', 'aaaccc','aaaddd', etc. You can otherwise set a custom separator; e.g. the '-' character: 'aaa-bbb', 'aaa-ccc','aaa-ddd'.
- Other words. With this attribute, similarly to 2., you can set rules for the other words of a phrase.
- Postfix - text that will finalize each phrase. For example, if you set Postfix to the '?' or ' ?', all phrases created with this rule will have the question mark at the end.
If you activate the mutation option for the first time, the program will suggest the following rules by default:
| Rule |
Example |
| string1=firstupper|stringN=lower |
Ilovemycomputer |
| string1=firstupper|stringN=firstupper |
ILoveMyComputer |
| string1=lower|stringN=lower|delimiter=t20 |
i love my computer |
| string1=firstupper|stringN=lower|delimiter=t20 |
I love my computer |
| string1=firstupper|stringN=firstupper|delimiter=t20 |
I Love My Computer |
Naturally, the more mutation rules you set, the wider is the range of phrases you generate, and the more chances you get for the successful recovery of the original password. On the other hand, if the range is large enough, when searching through the entire range may take half an hour or more, the program will highlight the statistics text with red color. There's no reason to be afraid of that. Simply select one of the source dictionaries of a smaller size or decline from some mutation rules or, leave everything the way it is.
The 'Statistics' group shows the average/recommended size of the dictionary, number of words in source dictionaries, total the number of passwords being generated, and other helpful information.
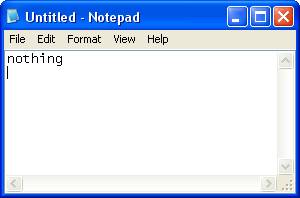
Let's take a look at a specific task. Suppose, we are to find a password of three words, the first one of which is 'nothing' with some punctuation mark at the end. Here is our plan:
| 1 Create a text file with the only 'nothing' word in it. That will be our primary dictionary. |
|
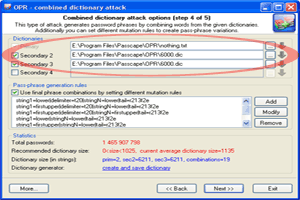
2 Select some general dictionary for the 1-st and 2-nd auxiliary dictionaries. For instance, the dictionary that comes with the program. |
 |
|
 |
|
|
|
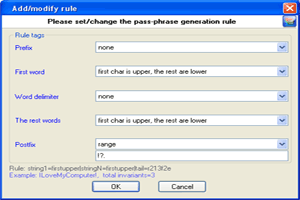
| 3 Set additional mutation rules. |
|
4 Launch the combined attack and wait for the result. |
 |
|
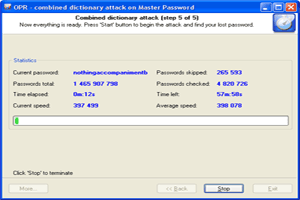 |
You can also download additional dictionary modules from the Passcape Software Web site.


 Perfect dictionaries for the combined passphrase attack are those that have different forms of words in them; e.g. jump, jumper, jumped, jumping.
Perfect dictionaries for the combined passphrase attack are those that have different forms of words in them; e.g. jump, jumper, jumped, jumping.



