Reset Windows Password:
recovering domain cached passwords
Setting search and recovery methods
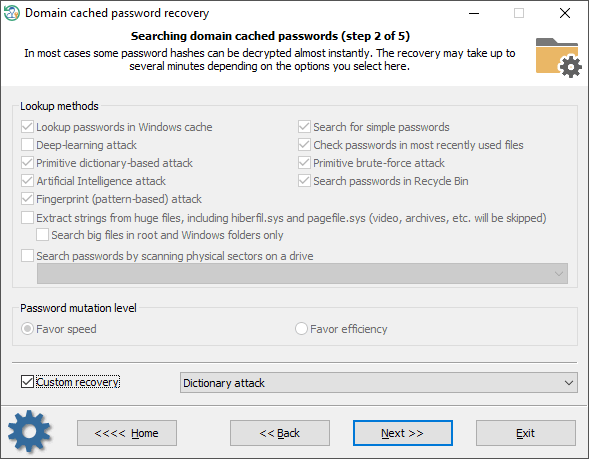
Domain cached password recovery consists of several modules. Each one can be turned on/off separately:
- Finding information in the Windows system cache. This module consists of over a dozen of mini-attacks, during which the program analyzes all kinds of system passwords: LSA secrets, DSL, FTP, LAN, WAN passwords, Internet and email credentials, etc. Later the found passwords are used in the program to guess other passwords by generating more complex variations.
- Analyzing simple, short and numeric passwords, keyboard combinations, etc. Over 20 mini-modules in total.
- Scanning, reading and analyzing most recently used files of the target system. The program parses the files and creates a list of words (by generating various mutations) to be checked as passwords.
- Primitive dictionary attack. The application checks all passwords from the built-in dictionary for the Light and Standard editions or from several dictionaries (Arabic, Chinese, English, French, German, Portuguese, Russian, Spanish) for the Advanced Edition. If the deep search option is on, simple word mutations will also be taken into account during the search.
- Primitive brute-force module that consists of several simple attacks to search for short passwords.
- Artificial Intelligence module analyzes network activity of users on the target computer. Over thirty mini-modules take care of that. Upon the results of the analysis, the application generates user preferences and creates a semantic dictionary for the attack. Then the dictionary is used for guessing passwords.
- Looking for passwords in deleted files.
- Primitive Fingerprint attack on English passwords. This module may take a lot of time to complete.
- Extract strings from huge files: RAM images, hiberfil.sys, pagefile.sys and so on. The program can skip files useless in password analysis like video, archives, audio files, etc.
- Searching for passwords by reading and analyzing raw sectors of the selected drive. If the Password mutation level is set to 'Favor efficiency', the program additionally tries to mutate all found passwords as well, thus walking through all sectors of the target drive may take quite a time. This module is not effective for drives that have a full-disk encryption set on. Like BitLocker or TrueCrypt, for example.
To apply a custom recovery method, turn on the 'Custom recovery' and select one of the available attacks. During the next steps, you will be prompted to set up and execute the selected attack.
Selecting data source
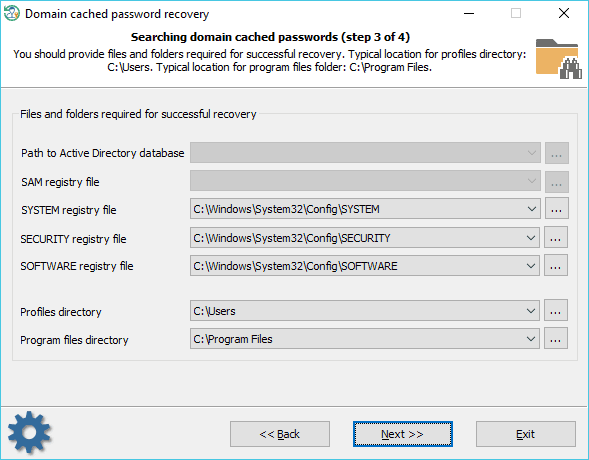
When searching for domain cached passwords, special attention is to be paid to proper setting files and folders required for the process. Reset Windows Password finds the files automatically, but sometimes, e.g., when the computer has several operating systems installed, you may need to adjust it manually. Also keep in mind that if the target PC has 2 or more hard disk drives, the sequence of the letters for these disks can be set totally differently than in the original system.
Searching for domain cached passwords
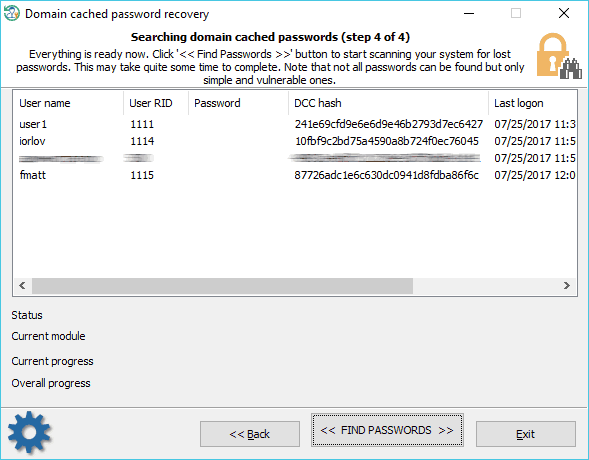
Domain cached credentials are of two types. DCC type 1 has very weak encryption and was used in Windows 2000, Windows XP and Windows 2003 OSes. Recovery rate can exceed millions or even billions of passwords per second. DCC type 2 is used in Windows Vista and later operating systems. Its encryption is much much stronger and quite resistant to cracking. The brute-force speed is only hundreds/thousands of passwords per second. Just imagine, guessing an 8 character long password consisting of upper and lower case letters using brute-force attack might take over 1000 years!
Do take into account the following considerations:
- The process of searching for DCC type 2 is extremely slow. Completing some modules (for example, Fingerprint attack) may take hours or even days.
- To speed up the search, select the only account you need the password for. Just right-click the cached entry and select 'Exclude from search all entries except selected'. Otherwise, the speed of the password recovery will decrease by a multiple of the number of accounts.